This guide talks about setting your enterprise Keycloak as a way your employee can log into their Google Workspace.
Most of the guides online talk about how to use Google as an identity provider for KeyCloak. The only one I found about using Keycloak as identity provider to Google was outdated and did not work. So I wrote this article.
Keycloak setup
First, create a new SAML application using the following config:
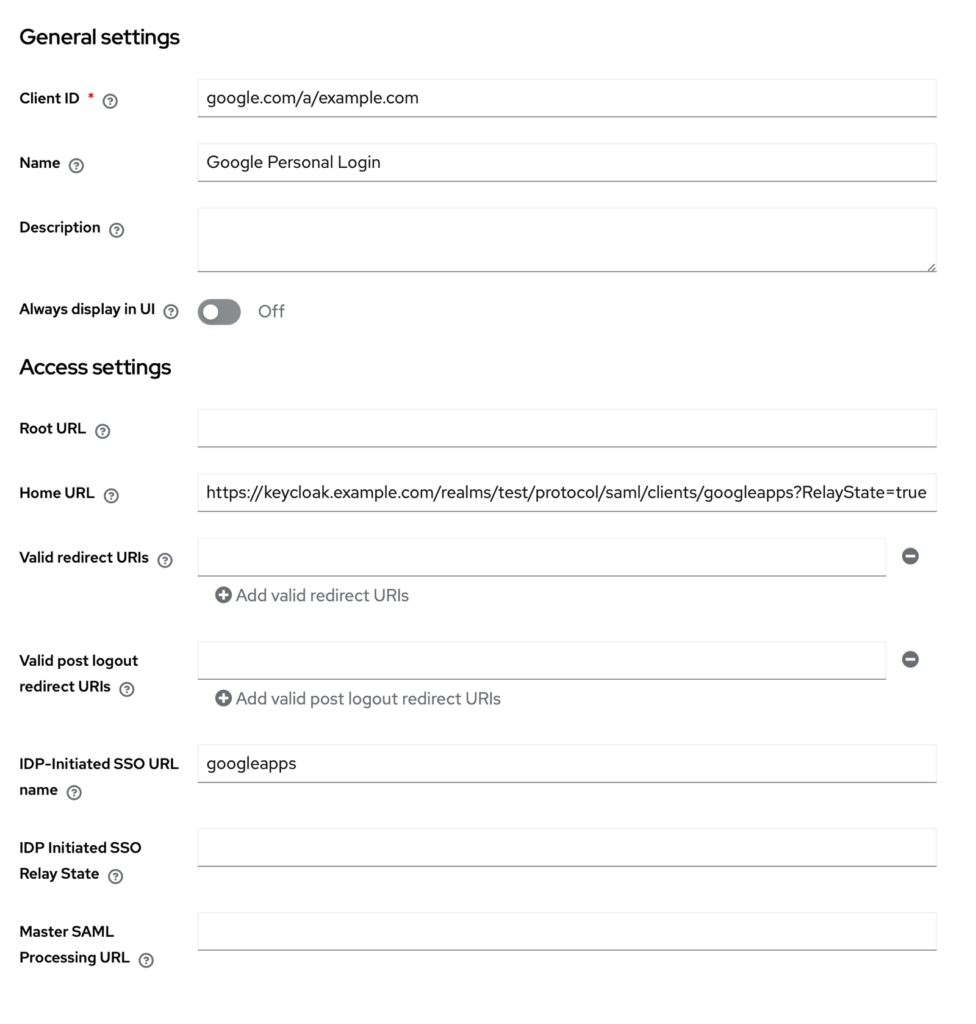
Remember to replace example.com with your Keycloak domain.
Now, Google requires an email mapping. This means, if you have an account in Google Workspace with email [email protected], you will set the email property of that user in Keycloak to be [email protected] and set the below SAML capabilities / Name ID format to email.
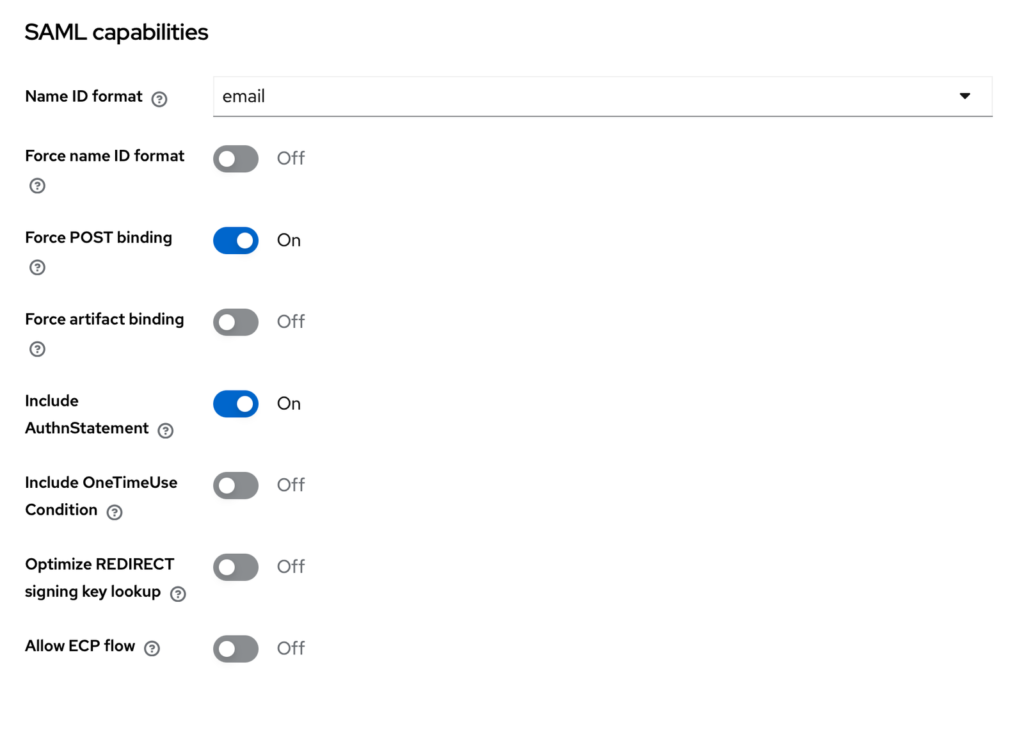
Make
Choose legacy SSO profile, Assertion Consumer Service (ACS) URL for single sign-on (SSO) is typically in the following format:
https://accounts.google.com/a/{domain.com}/acs
The rest of the configuration can stay untouched.
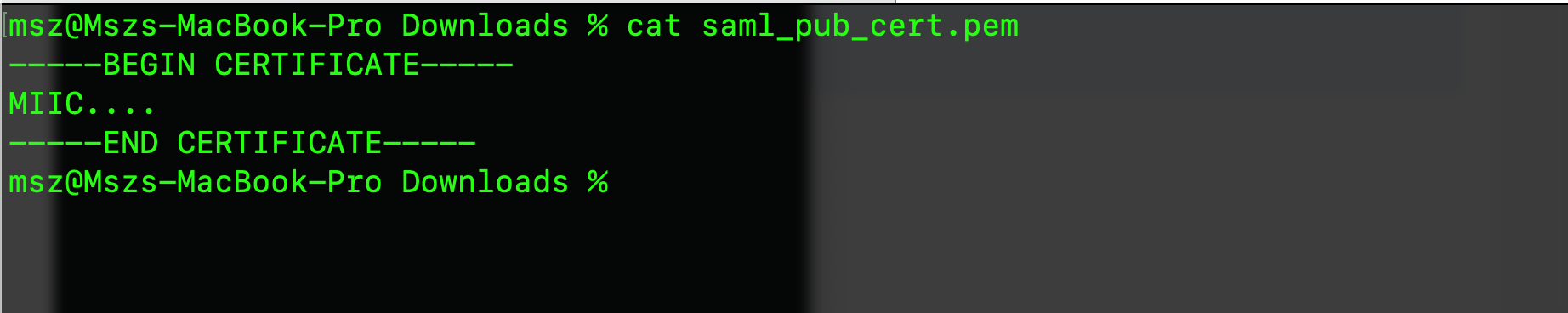
After creating the application, open it, and go to the Keys tab to copy the certificate to a new file called saml_pub_cert.pem
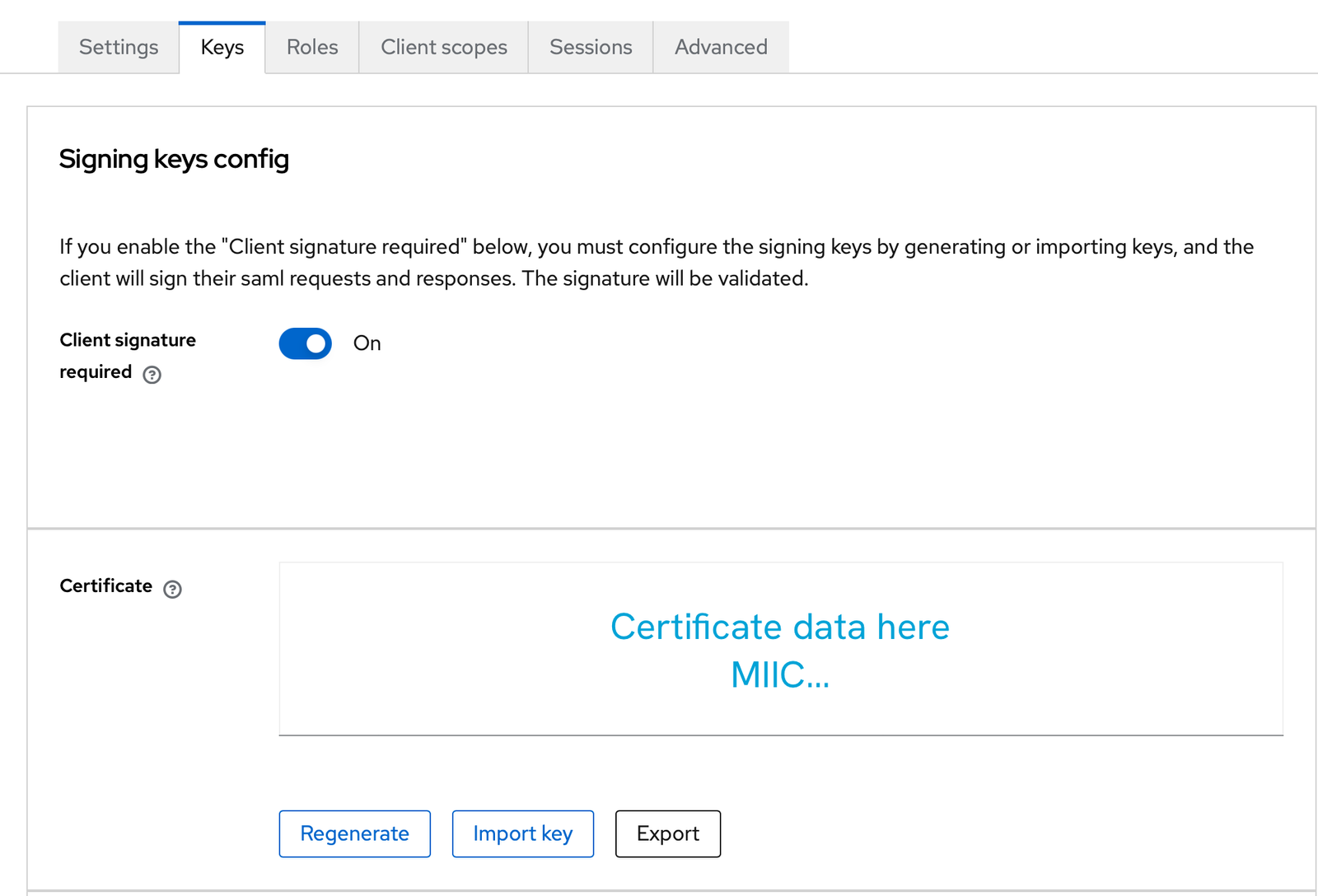
Now, in the file, make sure you include --—BEGIN CERTIFICATE----- in the beginning and --—END CERTIFICATE----- at the end of the line. Like this:
Configuration on Google
Go to your Google admin portal. And go to the Security >
SSO with third-party IDPs.
On the tap, tap to create a profile in the Third-party SSO profile for your organization section, and open Legacy SSO profile (SAML)
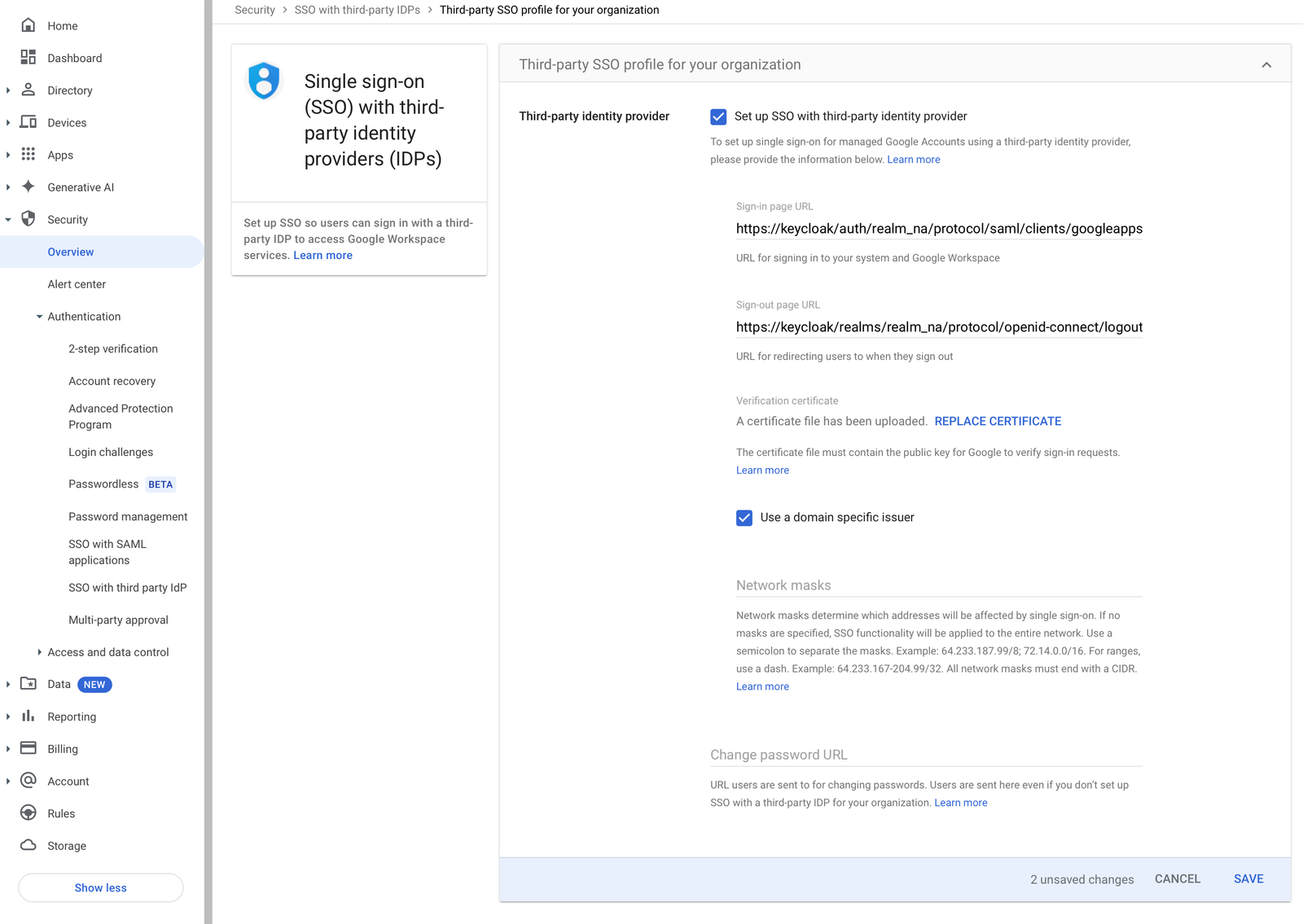
For the certificate file, upload your saml_pub_crt.pem
Save the changes.
Go back to “SSO with third party IDPs” and set the SSO profile assignments to legacy SSO.

Login
Now, access this URL:
https://your_keycloak_domain.example.com/realms/your_realm/protocol/saml/clients/googleapps?RelayState=true
Make sure you include RelayState. If you’re using Authentik, you should set RelayState in provider settings, advanced protocol settings section to any value.
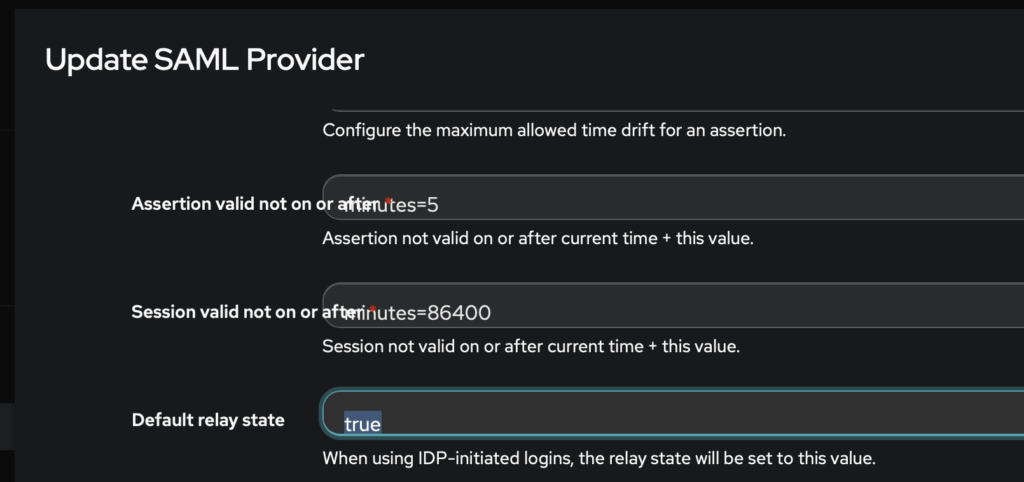
And you should be able to login.
There might be an issue where after logging in, it shows this page:
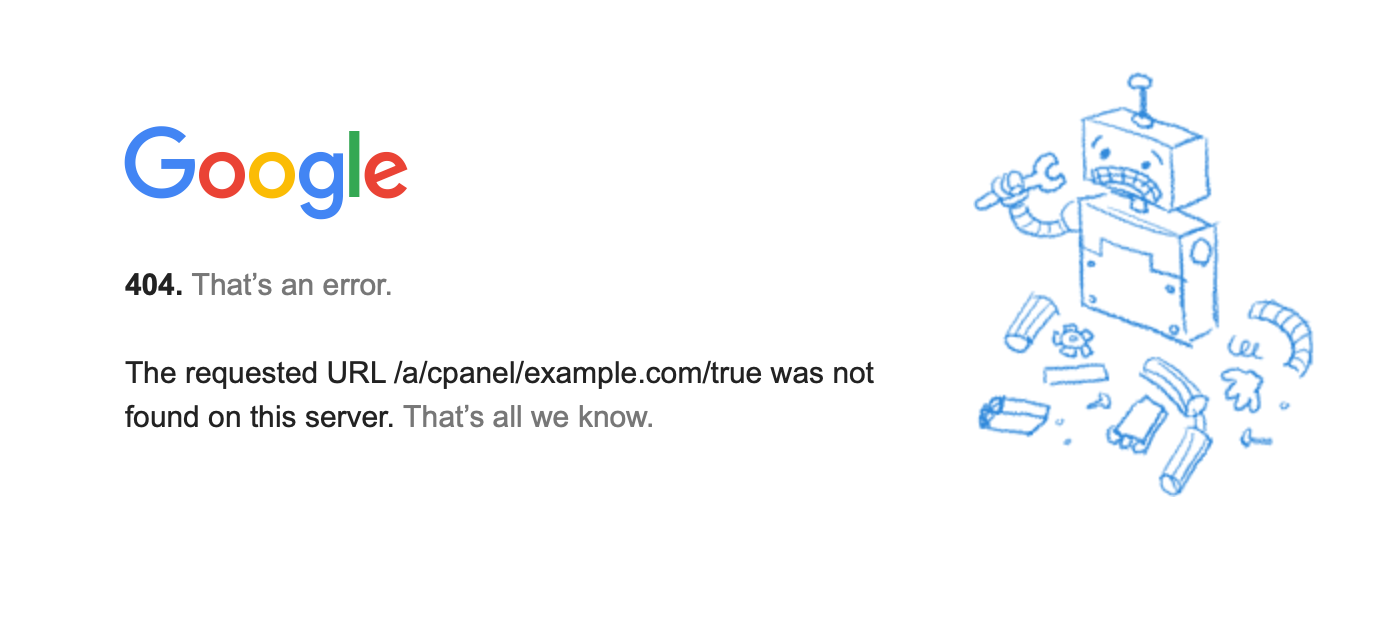
While I have not figured how to solve this yet. You are already logged in. You can navigate to google.com or gmail and you will see that you have logged in via Keycloak identity.
